5 Most Common File Types Used in Cyber Attacks
Threat actors are always inventing new ways to deliver malware. However, most of these methods involve one of a few common file formats. Recognizing that these may contain an infection mechanism and taking precautions by analyzing them in a sandbox can help you avoid falling victim to cyber attacks. Here are five of the most widely employed file formats by attackers.
Executable Files (.exe)
Executable files, identified by the .exe extension, are the foundation of Windows systems. This is also the file type that gets exploited in malware attacks the most.
Since .exe files contain binary code, they can instantly perform a wide range of malicious functions upon execution.
All an attacker needs to do is trick the victim into launching the file. They can achieve this in various ways, from orchestrating multi-stage attacks that begin with a seemingly harmless document to simply naming a malicious executable after a legitimate program.
To determine if an .exe file poses a threat, it’s crucial to analyze it in a sandbox.
ANY.RUN is a cloud-based sandbox that can provide you with a conclusive verdict on any file in seconds.
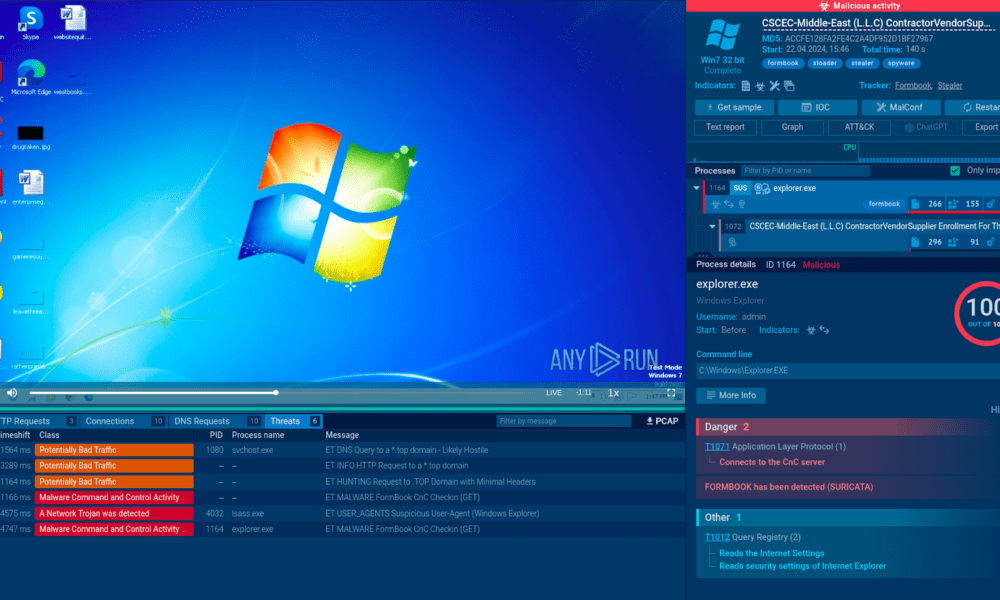
Here’s an example of a sandbox analysis of an executable file:

Formbook .exe file analysis session in the ANY.RUN sandbox
The service provides a real-time display of all processes taking place on the system. It shows that although there were no visible signs of infection on the screen, the execution of the .exe file resulted in the Formbook malware being covertly installed on the device. The network analysis segment also reveals that the malware makes a connection to its command-and-control (C2) server to receive further instructions.
PDF Files (.pdf)
PDF files, a staple of corporate environments and digital communication, offer a versatile and platform-independent way to share documents. This versatility is also the weakness that makes it an attractive target for malicious actors.
PDF files can contain a variety of elements, including images and links, which cybercriminals can use to facilitate their attacks.
Here’s an analysis of a PDF with an embedded malicious link:

A .pdf attack that installs NJRAT on the victim’s system shown in the ANY.RUN sandbox
The analysis in the ANY.RUN sandbox makes it possible to expose multi-state attacks that require human interaction, which is impossible to do in an automated sandbox.
In this case, we upload a suspicious .pdf file which is designed by attackers to look like an official document of Colombia’s Ministry of Transporation to the service and click a link which it contains. This action triggers a download of an archive with a VBS script file inside. Once executed, we can observe an NJRAT malware infection happening on the system.
Microsoft Office Files (.doc, .xls, .ppt)
Microsoft Office files are another go-to choice for threat actors. Analysts continue identifying new vulnerabilities in office documents every year, despite them having been around for over three decades.
Macros written in Visual Basic for Applications (VBA) constitute the number one method of abusing .doc and other office suite file types. These can be leveraged to download and install malware even without the user’s notice. In the case of Excel, attackers prefer to employ Excel 4.0 macros to deliver malware.
There are also numerous vulnerabilities that are abused by attackers. For instance, the CVE-2017-11882 vulnerability lets threats exploit Microsoft’s Equation Editor.
Let’s see a sandbox analysis of one such file:

A Suricata ruled used for detecting Agent Tesla shown in ANY.RUN
The sandbox exposes the attack that relies on the CVE-2017-11882 exploit, tracing the entire infection chain. We can clearly see how the launch of an .xla file led to the Agent Tesla malware being deployed on the system. The ANY.RUN sandbox also shows the triggered Suricata rule which detected Agent Tesla’s attempt to steal information from the infected device.
ZIP Files (.zip)
ZIP files are used to hide malware, allowing it to bypass basic detection systems and mislead users into believing the archive is risk-free due to the lack of antivirus notifications or warnings.
Since archives are frequently attached to phishing emails, they may have various names that fit the email’s subject matter, such as “invoice”, “notice”, or “documents”.
After opening a malicious archive, the victim may encounter a range of file types, from .exe and .doc ones to .png images that can be manipulated through steganography. As soon as they execute one of them, the infection process will begin.
See how an attack involving an archive file unfolds in this analysis:

An analysis of an njRAT attack in ANY.RUN
In addition to .zip files, there are several other popular archive formats used by attackers. In this case, we are dealing with a .rar file that contains two more archives. Inside them, we find malicious .vbs scripts that, upon execution, kickstart an njRAT malware infection.
Dynamic Link Libraries (.dll)
Dynamic Link Libraries (DLLs) are a type of executable file used by Windows operating systems that contains code which can be shared by multiple applications simultaneously.
Attackers exploit DLLs in different ways. One common technique is DLL hijacking. It involves replacing a legitimate DLL file with a malicious one that has the same name and file path. This lets threat actors gain the same privileges as the application on the system.
Here is a real-world example of how malware can exploit DLLs:

A Suricata rule used for detecting the Gh0st RAT in ANY.RUN
ANY.RUN lets us not only observe the real-time execution of an attack facilitated by a .dll file, but also interact with the system. The service instantly labels the file as exhibiting malicious activity and the built-in Suricata engine detects that the malware behind the attack is the Gh0st remote access trojan.
Analyze Files and Links in ANY.RUN
Proper security starts with proactive measures. Analyzing suspicious files and URLs in the ANY.RUN sandbox will help you avoid infection and get a detailed look at their malicious behavior. The service delivers conclusive results in under 40 seconds, helping you quickly make important security decisions.
Sign up for a free ANY.RUN account and enjoy unlimited analysis!





